Security – What is It Really All About?
Digital security has become a bit of a buzzword lately – but what does it really involve? Here are the answers to all those questions you’ve been too afraid to ask.
Why is Digital Security a Thing?
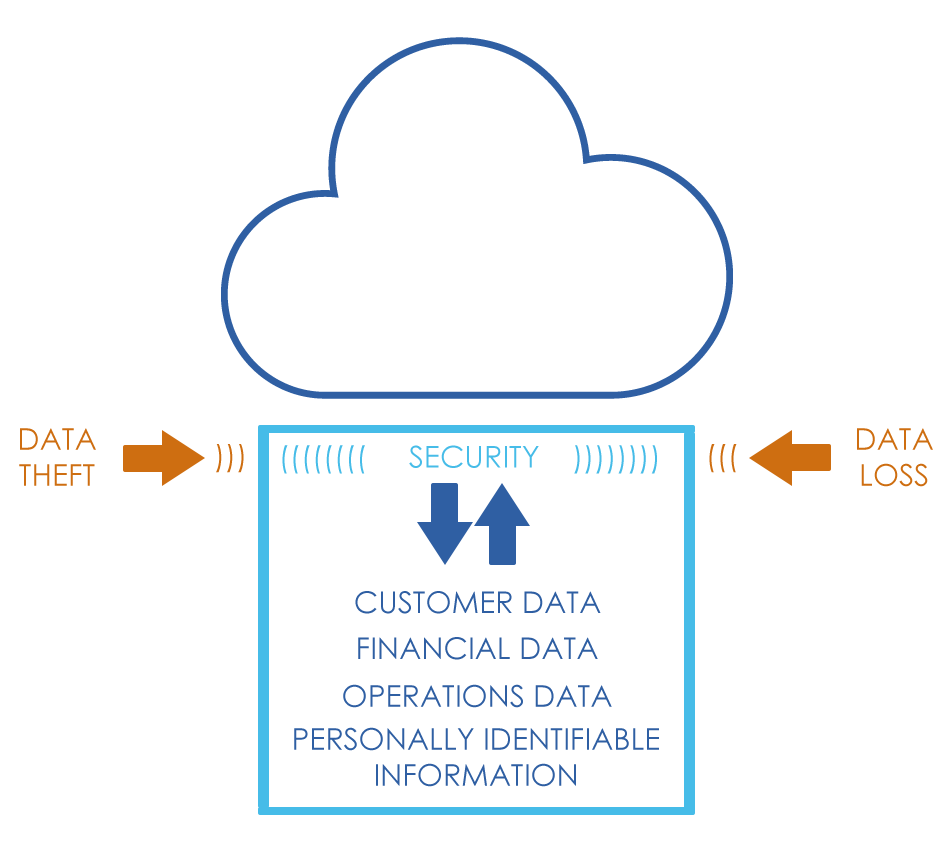
Whether you know it or not, you’ve probably entrusted a lot of personal information to “the cloud”. This catchall term essentially refers to any data that can be accessed online – that includes your online banking app, Amazon orders, electronic bill pay services, and even your iTunes library. This is where data security comes in – if you can access it digitally, there’s a chance it could be hacked.
While that sounds a little scary, don’t unplug your computer yet. Cloud based services are critical to how we live our lives, and if you choose carefully, can be a safe and secure convenience. How can you choose wisely?
Digital security keeps your data safe from threats including loss and theft.
Choose Services Wisely
If you’re going to entrust critical data to a service, you want to be certain it’s going to be safe. This is true whether you’re talking about personal details or proprietary business information. One of the best ways to do this is to trust tried and tested infrastructure.
Digital security is one of the highest paid fields in IT for a reason. New methods of attack that demand new safeguards are constantly appearing. This means that complex protocols, regular testing, and vigilance are essential, and small providers simply don’t have the resources to keep up.
Don’t worry though, that doesn’t mean that data security means only supporting the Walmarts and Amazons of the world. Smart small businesses utilize the infrastructure developed and maintained by larger companies. A great example of this is companies that use WooCommerce or Shopify for their e-commerce needs. For a monthly fee, small retailers are able to guarantee that their customer data is secured to a much higher level than they would be able to insure on their own. It’s a good idea to look for this information before making a purchase on an unfamiliar website.
SaAS (software as a service) companies, such as AvSight, have a similar choice to make. They can develop their own security protocols, or they can choose to build off of the solutions implemented by a tested and trusted company. AvSight opted to do the latter – our best in industry platform was developed on Salesforce’s proven infrastructure. That way, we can focus on what we do best – developing solutions to give our customers a competitive edge – while being confident that they’re data is as secure as possible.
Look for Certifications
The most trusted companies augment their rigorous internal testing with external certifications. Whether or not they apply to your industry, prestigious certifications such as HIPAA, GDPR, FedRamp, and DoD IL4, indicate that a company has achieved a very high level of security compliance. AvSight is proud that these certifications are among the 33 different international security certifications held by Salesforce. Since our platform is Salesforce native, it also achieves compliance with all of these certifications.
Understand Your Provider’s Infrastructure
When examining certifications, make sure you understand how your SaAS provider’s hosting infrastructure works. Many hosting environments, such as AWS, use a “shared responsibility model” for security. This means that they use robust security protocols to store data on their end, however the SaAS provider is responsible for what they build on top of that infrastructure – i.e. the actual cloud based service you are using. This can create points where your data is vulnerable.
Other environments essentially allow developers to build their service within their secure framework. AvSight uses this model to benefit from Salesforce’s extensive security development.
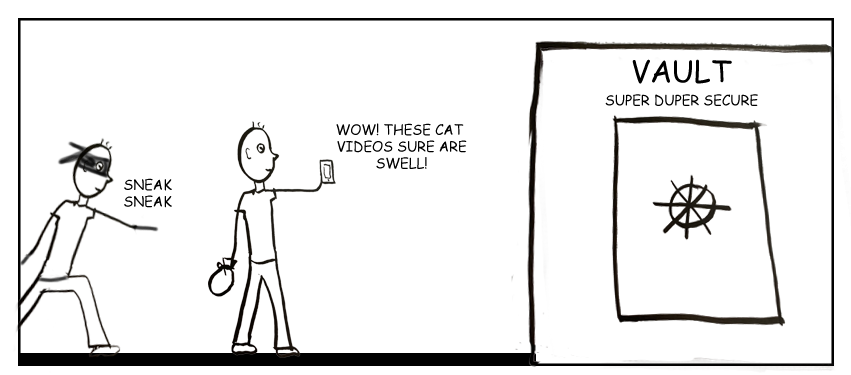
To illustrate the difference, imagine that you have to transport valuables to a state of the art vault. The shared responsibility model means that you’re responsible for transporting your valuables securely to the vault. If you mishandle the items while they’re in your possession, they will be vulnerable, regardless of how secure the vault is.
But, with the second model – building a service within a secure framework – you are essentially just transporting your valuables from one side of the vault to the other. Since they never leave the security of the vault, there is little chance that they can be mishandled.
Don’t Forget Internal Security
External security protocols are of little value if internal security is lax. If you use cloud services for business, your data should not visible to your service provider. This limits the risk of accidental exposure. It’s also important to be sure that you have the ability to set security rights for your employees. This reduces the chance of data being exposed accidentally or maliciously by an employee.
With AvSight, your data is encrypted and inaccessible to our team. Our platform also supports the creation of user rights to ensure that only necessary data can be accessed by employees. Check out more about our security protocols here.
The Bottom Line
Regardless of functionality, a service is only as good as it’s security. Make sure you do your research ahead of time to prevent future issues. Also, if you’re in the aviation aftermarket industry, choose AvSight. We offer the most secure and functional ERP in the business.
Experience AvSight for Yourself
Request a demo to see how our next generation aviation platform can give your company a competitive edge.
Request A Demo